Developers Day CTF Walkthrough
Assalum Alikum, This is Rehan Mumtaz from NED university . It is my first writeup for CTF challenges walkthrough . Our team m4lware ended up on 4th place on the leaderboard submitting all the flags 🙌

ACM FAST-NUCES organized ethical hacking competition on their Developers Day event. It was jeopardy-based ctf, comprising of categories :
Web Exploitation
1. Cattos are cute

Here we have been given a website link, on checking the source code it does not seem interesting. On looking over to its robots.txt page

Flag seemed to be ROT19 encoded, simple decode it! FastCTF{t00_e45y_f0r_y0u_1_th1nk}
2. Just CTRL+C, V the flag

In this challenge, I again checked the source code and find this link interesting
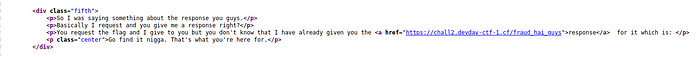
I opened it but it gave me a blank page, I fired up my burp and check the response header and I got the flag
FastCTF{wh4t_k1nd_0f_r35p0n53_15_th15}
3. Challenges & Scores

In this challenge, we have to find a user id to see its challenges while one id was given

So whynot try entering something like this to see all id’s challenges
P.S : Here is SQLi vulnerability
‘ or 1 = 1 — -
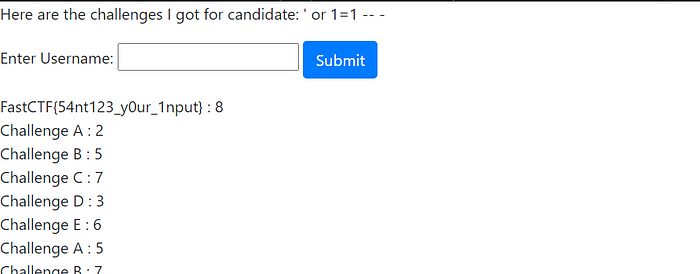
FastCTF{54nt123_y0ur_1nput}
4. Your Wish is my command
In this challenge, there is a command injection vulnerability ,there was an input box given where can we run certain commands while the page showed the output so , using
ls -la & cd hidden & cat flag.txt
since the page shows all page empty (white font color), i checked the source code and got the flag
Steganography
1. How To Survive

we were given a png file , runnig strings command did the work
FastCTF{m0v1ng_f0rw4rd_15_th3_0nly_w4y_t0_5urv1v3}
2. Meta Meta where are you
Png file was given, i ran exiftool on it

Comment entry seemed encoded to me i tried ROT47 to decode this comment
FastCTF{th15_15_ju5t_f0r_w4rmup}
3. Doge Looks Sus

jpg file was given i ran steghide tool to decode it but it was asking for a passphrase so i run exiftool on it

again comment contain passphrase base64 encoded and I decode it and pass it to steghide and I got the flag
FastCTF{1t_w45_r34lly_345y}
4. Wiki Search for Dogs

In this challenge, we have given a website which contains different pictures of dogs and their description, so first of all i checked the source code and try brute forcing directories, then after getting no breakthrough I tried each & every picture, may be something is hidden inside the pictures.

I run binwalk on 2nd picture, I extracted the zip folder which is passwd protected and I run frackzip to bruteforce password and got the secret.txt which has the flag
FastCTF{54y_ch3353}
Cryptography
1. Based Like You

Encoded Message is base64-encoded I decode it and got the flag
FastCTF{345y_t0_845364}
2. The Whisper

Morse code was given so I uses online tool to decode it https://morsedecoder.com/

I tried ROT-13 decode and got the flag
FastCTF{1T_D1FF1CULT_T0_G3T}
3. Baby RSA

we were given a text file

I used https://www.dcode.fr/rsa-cipher to decrypt the flag
FastCTF{h3h3h3_y0u_kn0w_RSA}
4. Can’t be done

Since the cipher name is encoded two times, after many tried i got ROT47 decode and ROT13 decode to give the clear cipher name
Nihilist
I used https://cryptii.com/ to decrypt the text

FastCTF{putin_says_cyka_blyat}
Reverse Engineering
~ solved by Saad Akhtar
1. Babiest reverse

We got a binary file from the challenge.
Running the file command returns the following
It’s a 64-bit ELF binary.
Method 1:
Method 2:
2. Baby Reverse

Running the file command
Executing the file, we can see that it’s asking for a magic number and then returns Nice Try! On a wrong attempt.
Analyzing the binary with Ghidra.
In the main function, we have a function verify.
Looking at the verify function, in line 8, we have a comparison with a hex value (the first magic number)
Convert that hex value to decimal
Further we can see in line 12, we have a check function.
Looking at the check() function
Here again, we have a comparison with a value.
Convert that hex value to integer and we’ll get our 2nd magic number.
Submitting the magic numbers, we’ll get the flag in reverse format.
Reversing string with python
3. Mathematical Reverse

We have a binary file, running the file command.
Executing the file.
We have to enter a magic number and on wrong attempt, we are given a fake flag.
Analyzing the file with Ghidra.
In the main function, we can see an if statement in line 44 below.
Here local_34 is the input variable’s value.
Converting the hex to integer.
If we input the same number above, the if statement will get true and we’ll get our flag.
4. Malware
~ solved by @Mohammad haris

Download the given file,after downloading it we can see that its has an extension of .pyc which represents a python file in byte code. Lets convert this file to a normal .py file using an online decompiler (toolnb.com)
after the challenge i learned about a python library which does that offline which is uncompile6 which we can download using command
pip install uncompyle6
Now lets make a new .py file and copy the code over there
As we can see that their are many variables declared over here with different encoded strings but the last variable trust has them all combined and encoded into a single long string but it is not printed so we cant see any output so in order see output we would print the variable and the result we get is
aW1wb3J0IGNvZGVjcw0KDQpub2ZsYWcgPSAiWm55ajRlMyINCg0KaGFoYWZsYWcgPSAiXzRhbnlsZjFmfSINCg0Kd2hlcmVmbGFnID0gIm80b2xfIg0KDQp0ZXN0ZmxhZz0gIlMiDQoNCmZsYWcgPSAiU25mIg0KDQpsb2xmbGFnID0ieyINCg0KZmxhZyArPSAiZ1BHIg0KDQoNCmdldCA9IGludChpbnB1dCgiRW50ZXIgYSBtYWdpYyBudW1iZXI6ICIpKQ0KDQpmbGFnICs9IHRlc3RmbGFnICsgbG9sZmxhZyArIHdoZXJlZmxhZyArIG5vZmxhZyArIGhhaGFmbGFnDQppZiBnZXQgPT0gc3VtKFtvcmQoaSkgZm9yIGkgaW4gZmxhZ10pOg0KCXByaW50KGNvZGVjcy5kZWNvZGUoZmxhZywgInJvdF8xMyIpKQ0K
Its a base64 encoded string we can simply decode it using our terminal. The output we get after decoding the string is
import codecs
noflag = “Znyj4e3”
hahaflag = “_4anylf1f}”
whereflag = “o4ol_”
testflag= “S”
flag = “Snf”
lolflag =”{“
flag += “gPG”
get = int(input(“Enter a magic number: “))
flag += testflag + lolflag + whereflag + noflag + hahaflag
if get == sum([ord(i) for i in flag]):
print(codecs.decode(flag, “rot_13”))
Its another code with different variables again but on running the code i get errors so I came up with a solution as we can see that at the end its running a condition on a variable containing all the variable and if the condition satisfies it runs rot13 algo on it so i just print the main variable FLAG
The output we get is SnfgPGS{o4ol_Znyj4e3_4anylf1f}
It looks somewhat like a flag with those curly brackets but dosent makes any sense so i ran rot 13 over it & finally we get the flag
FastCTF{b4by_Malw4r3_4nalys1s}
